Weak and reused passwords are a persistent threat, especially after password dumps or internal audits. To help security teams make sense of cracked credential data, I’ve built the Cracked Password Complexity & Reuse Audit Tool that inspects cracked passwords for length, complexity, and reuse patterns. It generates a visual terminal report and an optional CSVContinueContinue reading “Password Complexity & Reuse Audit Tool”
Tag Archives: Password
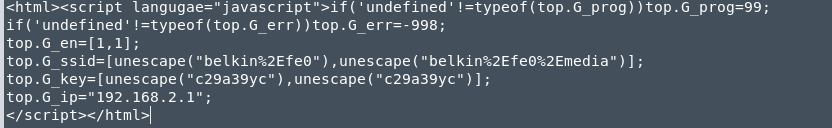
From Shodan to Remote Code Execution #3: Hacking the Belkin N600DB Wireless Router
Our newest post of this interesting series of Shodan to RCE takes us to Belkin routers. Shodan search: “Server: httpd” “Cache-Control: no-cache,no-store,must-revalidate, post-check=0,pre-check=0” “100-index.htm” As at the time of writing this post, there were not so many results for the Belkin routers )-: By navigating to one of the shodan search results, we may getContinueContinue reading “From Shodan to Remote Code Execution #3: Hacking the Belkin N600DB Wireless Router”