Weak and reused passwords are a persistent threat, especially after password dumps or internal audits. To help security teams make sense of cracked credential data, I’ve built the Cracked Password Complexity & Reuse Audit Tool that inspects cracked passwords for length, complexity, and reuse patterns. It generates a visual terminal report and an optional CSVContinueContinue reading “Password Complexity & Reuse Audit Tool”
Author Archives: Alfie
Cisco Configuration File Auditing Tool (ccfat) : Automating Cisco Configuration Audits
Introduction Network security and performance depend heavily on correctly configured devices, especially Cisco routers, switches, and firewalls. A single misconfiguration can introduce vulnerabilities, create inefficiencies, or lead to compliance failures. Manual audits are time-consuming and prone to errors, but automation can change the game. The Cisco Configuration File Auditing Tool offers a seamless way toContinueContinue reading “Cisco Configuration File Auditing Tool (ccfat) : Automating Cisco Configuration Audits”
FortiGate Configuration Files Audit Tool (fcfat): Enhancing Firewall Security with Automated Analysis
Introduction Conducting regular audits of firewall configurations is essential for ensuring compliance, identifying potential security gaps, and maintaining optimal performance. This is where the FortiGate Configuration Files Audit Tool (fcfat) comes into play. Developed to streamline the auditing process for Fortinet FortiGate firewalls, this tool provides an automated way to analyze configuration files, detect misconfigurations,ContinueContinue reading “FortiGate Configuration Files Audit Tool (fcfat): Enhancing Firewall Security with Automated Analysis”
Oracle EBS Security auditing
So this is my attempt to improve on this post I wrote last year and other tests that I find helpful. Whatever is outlined here really is a tip of the iceberg and further tests should definitely be done depending on scope, objectives… Application testing: Controls to test: Default application account credentials Weak application passwordContinueContinue reading “Oracle EBS Security auditing”
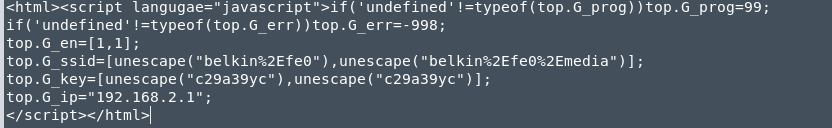
From Shodan to Remote Code Execution #3: Hacking the Belkin N600DB Wireless Router
Our newest post of this interesting series of Shodan to RCE takes us to Belkin routers. Shodan search: “Server: httpd” “Cache-Control: no-cache,no-store,must-revalidate, post-check=0,pre-check=0” “100-index.htm” As at the time of writing this post, there were not so many results for the Belkin routers )-: By navigating to one of the shodan search results, we may getContinueContinue reading “From Shodan to Remote Code Execution #3: Hacking the Belkin N600DB Wireless Router”
Blackhat Europe 2017 – conference notes
I had the pleasure to attend the Blackhat Europe 2017 in London – and it was enlightening! In this post, I shall provide links to the slide decks, videos and tools shared during the demonstrations, briefings and various talks. The abstracts for the briefings can be found on the official Blackhat Europe website. 1.Black HatContinueContinue reading “Blackhat Europe 2017 – conference notes”
From Shodan to Remote Code Execution #1 – hacking Jenkins
In this era of extreme automation, whether for development, programming deployment or even security management are we getting closer to security maturity or are we better off without the automation? In the next posts, I hope to uncover some of the tools/ applications employed on enterprises geared towards automation and better security but end upContinueContinue reading “From Shodan to Remote Code Execution #1 – hacking Jenkins”
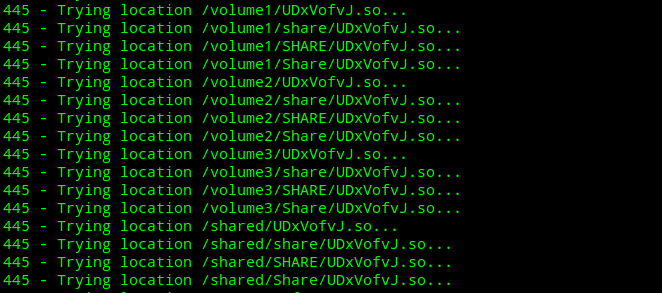
SAMBAry save us!!
Remember linux users laughing at Windows users because of the now all too famous Wannacry? Karma. According to Samba, “All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load andContinueContinue reading “SAMBAry save us!!”
From Shodan to Remote Code Execution #2 – hacking OpenDreambox 2.0.0
A sequel to the last post of what is now becoming a series of “From Shodan to remote code execution”, we now take a look at how to hack misconfigured Dreambox installations. Dreambox is a company which offers Digital TV set top boxes and other related services. Shodan search: Perform a shodan search as below:ContinueContinue reading “From Shodan to Remote Code Execution #2 – hacking OpenDreambox 2.0.0”
Exploiting Windows with Eternalblue and Doublepulsar with Metasploit!
Most of us got hold of the NSA exploits recently released to the public and there was so much hype and public statements around it. A lot has been said, and most vendors came out to defend their products and to release patches to downplay/mitigate the impact of these exploits. In the exploits, we cameContinueContinue reading “Exploiting Windows with Eternalblue and Doublepulsar with Metasploit!”